云安全性包含技术,控件,流程和策略,这些技术,控件,流程和策略结合起来可以保护基于云的系统,数据和基础架构。它是计算机安全性(更广泛地说是信息安全性)的子域。
这是您和您的云服务提供商之间的共同责任。您实施云安全策略来保护您的数据,遵守法规要求并保护客户的隐私。反过来又可以保护您免受数据泄露和数据丢失的声誉,财务和法律影响。
云安全共享责任模型(图片来源:Synopsys)
云安全性是所有组织的关键要求。尤其是根据(ISC)2的最新研究报告,有93%的组织对云安全性有中等或高度关注,并且四分之一的组织确认了过去12个月中的云安全事件。
只需移至Kinsta,即可将WordPress网站的速度提高200%。
今天免费迁移
在本文中,我们将创建有关云安全性的综合指南。您将探索迁移到云的安全风险,了解为什么需要云安全,并发现云安全最佳实践。我们还将涵盖诸如如何评估云服务提供商的安全性以及如何确定认证和培训以提高云安全性等主题。
让我们开始。
云安全性是所有组织的关键要求。有了这份详尽的指南,您可以了解更多有关它的内容,它如何工作,其风险以及最佳实践的信息! ☁️?
点击鸣叫
云安全如何工作?
云安全是技术,控制,流程和策略的复杂交互。高度个性化的做法可满足您组织的独特要求。
因此,没有一个单一的解释涵盖云安全“如何工作”。
确保云工作负载的模型(图片来源:HyTrust)
幸运的是,您可以使用一套广泛建立的策略和工具来实现强大的云安全设置,其中包括:
身份和访问管理
所有公司都应具有身份和访问管理(IAM)系统,以控制对信息的访问。您的云提供商将直接与您的IAM集成,或提供自己的内置系统。 IAM结合了多因素身份验证和用户访问策略,可帮助您控制谁有权访问您的应用程序和数据,他们可以访问什么以及他们可以对您的数据做什么。
人身安全
物理安全性是云安全性的另一个支柱。这是多种措施的组合,可防止直接访问和破坏云提供商的数据中心内的硬件。物理安全包括通过安全门,不间断电源,闭路电视,警报,空气和颗粒过滤,防火等来控制直接进入。
威胁情报,监视和预防
威胁情报,入侵检测系统(IDS)和入侵防御系统(IPS)构成了云安全性的基础。威胁情报和IDS工具可提供功能,以识别当前以您的系统为目标或将成为未来威胁的攻击者。 IPS工具实现了减轻攻击并向您发出警报的功能,因此您也可以做出响应。
加密
使用云技术,您正在与云提供商的平台之间来回发送数据,通常将其存储在其基础架构中。加密是云安全的另一层,可以通过在静止和传输时对其进行编码来保护您的数据资产。如果没有只有您才能访问的解密密钥,这可以确保几乎无法解密数据。
云漏洞和渗透测试
维护和改善云安全性的另一种做法是漏洞和渗透测试。这些做法涉及您-或您的提供商-攻击您自己的云基础架构,以发现任何潜在的弱点或漏洞。然后,您可以实施解决方案来修补这些漏洞并提高安全性。
微细分
微分段在实施云安全性中越来越普遍。这是将您的云部署划分为不同的安全段,直至各个工作负载级别的一种做法。
通过隔离单个工作负载,您可以应用灵活的安全策略以最大程度地减少攻击者获得访问权限后可能造成的损害。
下一代防火墙
下一代防火墙是云安全难题中的另一部分。它们使用传统的防火墙功能和较新的高级功能来保护您的工作负载。传统的防火墙保护包括数据包筛选,状态检查,代理,IP阻止,域名阻止和端口阻止。
下一代防火墙增加了入侵防御系统,深度数据包检查,应用程序控制以及对加密流量的分析,以提供全面的威胁检测和防御。
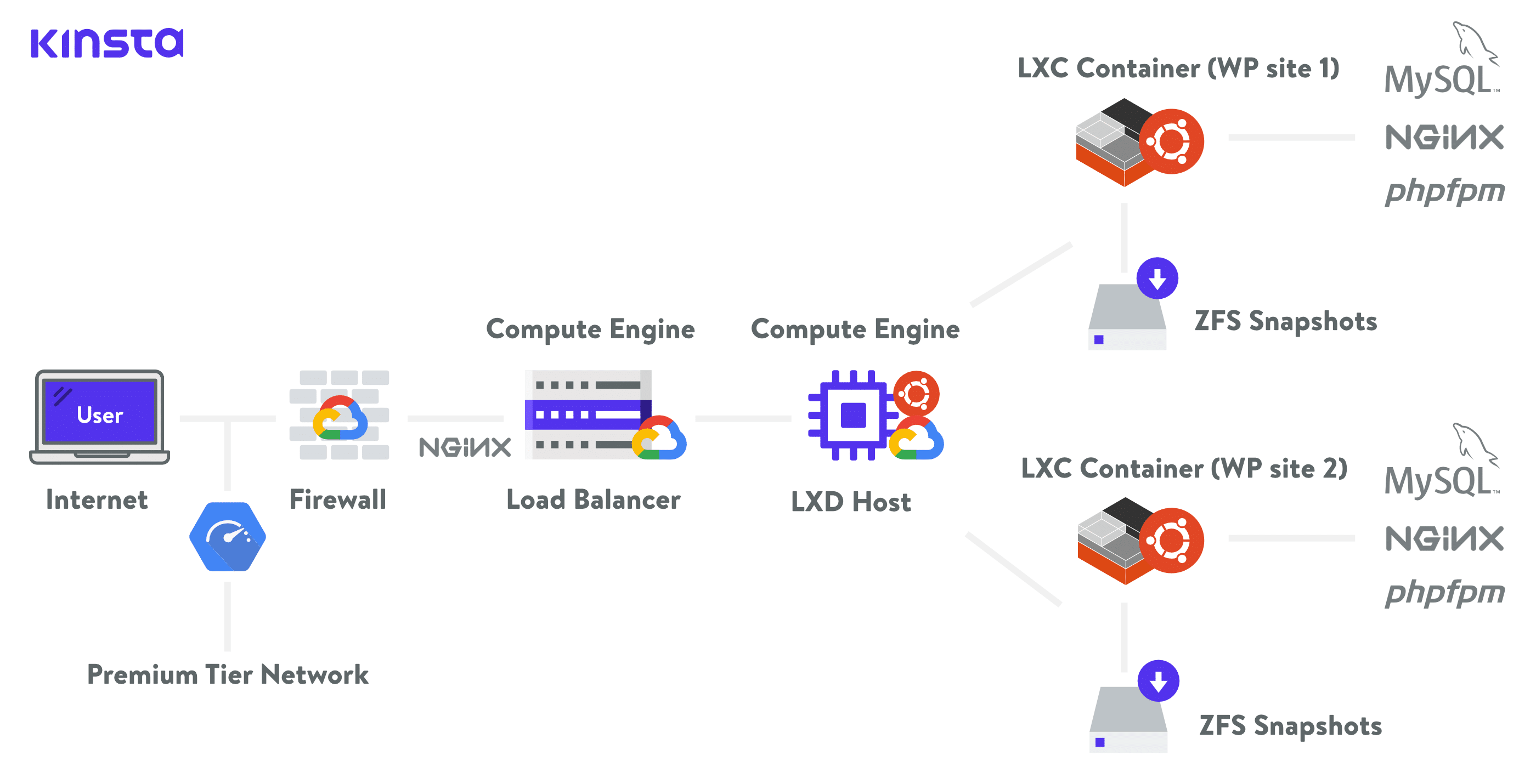
Kinsta托管架构
在Kinsta,我们在Google Cloud Platform(GCP)防火墙后面保护所有WordPress网站。提供最先进的保护,并能够与其他GCP安全解决方案更紧密地集成。
安全是所有企业都关心的问题,如果忽视它,则会严重影响声誉和底线。查看云计算的7种安全风险security️
点击鸣叫
7云计算的安全风险
无论您是否在云中运营,安全都是所有企业关注的问题。您将面临诸如拒绝服务,恶意软件,SQL注入,数据泄露和数据丢失等风险。所有这些都会极大地影响您的企业声誉和底线。
当您迁移到云时,会引入一系列新的风险并改变其他风险的性质。这并不意味着云计算并不安全。实际上,许多云提供商都提供了对高级安全工具和资源的访问权限,而这些是您无法访问的。
这只是意味着您需要了解风险的变化以减轻风险。因此,让我们看一下云计算的独特安全风险。
1.失去可见性
大多数公司将通过多个设备,部门和地理位置访问一系列云服务。如果没有适当的工具,那么云计算设置中的这种复杂性会使您失去对基础架构访问的可见性。
如果没有正确的流程,您将看不到谁在使用您的云服务。包括他们正在访问,上传和下载的数据。
如果看不到它,就无法保护它。增加数据泄露和数据丢失的风险。
2.违反合规性
随着法规控制的增加,您可能需要遵守一系列严格的合规性要求。迁移到云中时,如果不小心,会带来违反合规性的风险。
这些法规中的许多要求您的公司知道您的数据在哪里,谁可以访问它,如何处理它以及如何对其进行保护。其他法规要求您的云提供商拥有某些合规性凭证。
粗心地将数据传输到云或转移到错误的提供商,可能会使您的组织处于违规状态。引入潜在的严重法律和财务影响。
3.缺乏云安全战略和架构
您可以轻松避免这种云安全风险,但许多风险却无法避免。为了将系统和数据迁移到云中,许多组织早在安全系统和策略到位以保护其基础结构之前就已开始运营。
在Kinsta,我们了解了迁移到云时安全至上的心态的重要性。这就是为什么Kinsta提供免费的WordPress迁移,以确保您向云的过渡既安全又避免长时间停机的原因。
确保实施旨在使云与系统和数据保持同步的安全策略和基础架构。
4.内部威胁
您值得信赖的员工,承包商和业务合作伙伴可能是您最大的安全隐患。这些内部威胁不需要恶意意图即可对您的业务造成损害。实际上,大多数内幕事件源于缺乏培训或疏忽大意。
当您当前面临此问题时,迁移到云将改变风险。您可以将数据控制权交给云服务提供商,并从提供商的员工那里引入新的内部威胁层。
5.违约
您拥有的任何合同合作伙伴关系都将限制如何使用共享数据,如何存储共享数据以及授权谁访问共享数据。您的员工在未经授权的情况下不经意间将受限制的数据转移到云服务中可能会违反合同,从而可能导致法律诉讼。
确保您阅读了云提供商的条款和条件。即使您有权将数据移动到云中,某些服务提供商也有权共享上传到其基础架构中的所有数据。由于无知,您可能无意间违反了保密协议。
6.不安全的应用程序用户界面(API)
在云基础架构中的操作系统时,您可以使用API来实现控制。 Web或移动应用程序中内置的任何API都可以由员工内部提供,也可以由消费者外部提供。
面向外部的API可能会带来云安全风险。任何不安全的外部API都是网关,旨在为希望窃取数据和操纵服务的网络犯罪分子提供未经授权的访问。
不安全的外部API的最突出示例是Facebook – Cambridge Analytica Scandal。 Facebook不安全的外部API赋予Cambridge Analytica对Facebook用户数据的深度访问权限。
7.云服务的配置错误
云服务配置错误是另一个潜在的云安全风险。随着服务范围和复杂性的增加,这是一个日益严重的问题。云服务的配置错误会导致数据公开暴露,操纵甚至删除。
常见原因包括保留高度安全的数据的默认安全性和访问管理设置。其他措施包括不匹配的访问管理,可提供未经授权的个人访问权限,以及损坏的数据访问权限,无需授权即可打开机密数据。
为什么需要云安全
云技术的大规模采用以及不断增长的网络威胁和复杂的网络威胁,共同推动了对云安全的需求。反思上面概述的采用云技术带来的安全风险,若无法缓解这些风险可能会产生重大影响。
但这并不全都是消极的,云安全也可以带来巨大的好处。让我们探讨一下为什么云安全是至关重要的要求。
网络安全威胁持续增加
安全的云实践的驱动力是网络犯罪分子的数量和复杂程度不断增加的威胁。为了量化威胁,来自(ISC)2的云安全报告发现,有28%的企业在2019年经历了云安全事件。英国政府还报告说,在过去12个月中,有32%的英国企业遭受了系统攻击。
防止数据泄露和数据丢失
这些日益增加的网络威胁的结果是数据泄露和数据丢失的频率和数量的加速。仅在2019年的前6个月,诺顿新兴威胁报告就概述了超过40亿条记录被泄露的情况。
丢失或破坏数据泄露可能会产生重大的法律,财务和声誉影响。 IBM现在在其最新报告中估计,数据泄露的平均成本为392万美元。
避免违反合规性
我们已经提到过云安全如何带来违规风险。为证明违规的含义,您只需要观察德国联邦隐私监管机构,该机构最近就违反欧盟《通用数据保护条例》(GDPR)向1&1电信公司处以955万欧元的罚款。
维持业务连续性
良好的云安全性有助于维持您的业务连续性。防御诸如拒绝服务攻击(DDoS攻击)之类的威胁。计划外中断和系统停机会中断您的业务连续性并影响您的利润。 Gartner的一项研究估计,停机时间的平均成本为每分钟5600美元。
云安全优势
除了威胁防护和避免不当行为带来的后果外,云安全还提供了使它成为企业必需的优势。这些包括:
1.集中安全
与云计算集中应用程序和数据的方式相同,云安全也集中保护。帮助您提高可见性,实施控制并更好地防御攻击。将所有功能都集中到一处,还可以改善您的业务连续性和灾难恢复。
信息
Kinsta为每个计划提供安全保证,万一发生不良情况,安全专家将修复您的站点。
2.降低成本
著名的云服务提供商将提供内置的硬件和软件,以全天候保护您的应用程序和数据。这样就无需在您自己的设置中进行大量的财务投资。
3.减少管理
迁移到云引入了安全性的共享责任模型。这可以大大减少投入用于管理安全性的时间和资源。云服务提供商将负责跨存储,计算,网络和物理基础架构保护其基础架构(以及您)。
4.更高的可靠性
领先的云服务提供商将提供您可以依靠的尖端云安全硬件和软件。您将获得连续服务的访问权限,您的用户可以在任何设备上从任何地方安全地访问数据和应用程序。
云安全最佳实践
将系统移至云时,许多安全流程和最佳实践保持不变。但是,为了维护基于云的系统和数据的安全性,您将遇到一系列新的挑战。
为了帮助您应对这一挑战,我们针对基于云的部署编制了一系列安全最佳实践。
云安全性是计算机安全性(更广泛地说是信息安全性)的子域。查看这些基于云的部署的最佳实践! ☁️?
点击鸣叫
选择受信任的提供商
云安全最佳实践的基础建立在选择可信赖的服务提供商上。您想与提供最佳内置安全协议并符合最高水平的行业最佳实践的云提供商合作。
为您扩展合作伙伴和解决方案市场的服务提供商,以进一步增强部署的安全性。
值得信赖的提供商的标志体现在他们所拥有的一系列安全合规性和认证中。任何好的提供者都可以将其公开。例如,所有领先的提供商(例如Amazon Web Services,阿里云,Google Cloud(为Kinsta提供支持)和Azure)都提供透明的访问权限,您可以在其中确认其安全合规性和认证。
除此之外,选择受信任的提供者还有许多因素。我们将在本文后面的内容中介绍这十大清单,以评估任何云提供商的安全性。
了解您的共同责任模式
与云服务提供商合作时,将系统和数据移至云中时,您将建立起共同承担安全实施责任的伙伴关系。
最佳实践的关键部分包括审查并了解您的共同责任。发现哪些安全任务将留在您的手中,以及哪些任务现在将由提供商处理。
这是一个浮动比例,具体取决于您选择的是软件即服务(SaaS),平台即服务(PaaS),基础架构即服务(IaaS)还是本地数据中心。
Google Cloud Platform共同责任模式
AWS,Azure,Google Cloud Platform和阿里云等领先的云服务提供商发布了所谓的安全共享责任模型。确保透明度和清晰度。确保您查看了云服务提供商的责任共担模型。
查看您的云提供商合同和SLA
您可能不应该考虑将云合同和SLA视为安全最佳实践的一部分。 SLA和云服务合同仅是事件发生时提供服务和追索权的保证。
条款和条件,附件和附录中有很多内容可能会影响您的安全性。合同可能意味着您的云服务提供商负责您的数据和拥有它之间的区别。
根据McAfee 2019云采用和风险报告,有62.7%的云提供商未指定客户数据归客户所有。这将创建一个合法的灰色区域,提供商可以在其中声明对您所有上载数据的所有权。
如果终止服务,请检查谁拥有数据以及数据将如何处理。另外,请弄清楚是否需要提供者提供对任何安全事件和响应的可见性。
如果您对合同的内容不满意,请尝试进行谈判。如果有任何不可协商的内容,则需要确定同意对于企业而言是否是可接受的风险。如果不是,您将需要寻找其他选择,以通过加密,监控甚至选择其他提供商来降低风险。
培训您的用户
您的用户是安全云计算的第一道防线。他们的安全实践知识和应用可能是保护系统或为网络攻击打开一扇门的区别。
最佳做法是,确保对所有用户(员工和利益相关方)进行培训,这些用户以安全的云实践访问系统。让他们知道如何发现恶意软件,识别网络钓鱼电子邮件以及不安全做法的风险。
对于直接参与实施云安全性的更高级用户(例如管理员),请考虑针对特定行业的培训和认证。稍后,您会在指南中找到一系列推荐的云安全认证和培训。
控制用户访问
通过策略对用户访问进行严格控制是另一种云安全最佳实践。帮助您管理尝试访问您的云服务的用户。
您应该从零信任的位置开始,仅让用户访问他们所需的系统和数据,仅此而已。为避免实施策略时的复杂性,请创建具有指定角色的定义明确的组,以仅授予对所选资源的访问权限。然后,您可以将用户直接添加到组中,而不是为每个用户自定义访问权限。
保护您的用户端点
云安全最佳实践的另一个要素是保护用户端点。大多数用户将通过Web浏览器访问您的云服务。因此,至关重要的是,您必须引入高级客户端安全性,以使用户的浏览器保持最新状态并保护其不受攻击。
您还应该考虑实施端点安全解决方案以保护最终用户设备。随着移动设备和远程工作的爆炸式增长,至关重要的是,用户越来越多地通过非公司拥有的设备访问云服务。
寻找一种解决方案,其中包括防火墙,防病毒和Internet安全工具,移动设备安全性和入侵检测工具。
保持云服务的可见性
云服务的使用可能多种多样且短暂。许多组织在一系列提供商和地区中使用多种云服务。研究表明,云资源的平均寿命为2小时。
这种行为会在您的云环境中造成盲点。如果看不到它,则无法保护它。
确保您实现了可提供整个生态系统可见性的云安全解决方案。然后,您可以通过一个门户监视和保护您所有不同资源,项目和区域中的云使用情况。这种可见性将帮助您实施精细的安全策略并减轻各种风险。
实施加密
无论您身在何处,数据加密都是安全的最佳做法,这对您移至云中至关重要。使用云服务,您可以将数据存储在第三方平台上并在网络和云服务之间来回发送,从而使数据面临更大的风险。
确保对传输中的数据和静态数据实施最高级别的加密。您还应该考虑使用自己的加密解决方案,然后再将数据上传到云中,并使用自己的加密密钥来保持完全控制。
云提供商可能会提供内置的加密服务,以保护您的数据免受外界的攻击,但是它使他们能够访问您的加密密钥。
Kinsta采用完全加密的方法来进一步保护其安全的WordPress托管解决方案。这意味着我们不支持FTP连接,仅支持加密的SFTP和SSH连接。
实施强大的密码安全策略
无论您要访问的服务是什么,强健的密码安全策略都是最佳实践。实施尽可能强大的策略是防止未经授权的访问的重要因素。
作为最低要求,所有密码都应包含一个大写字母,一个小写字母,一个数字,一个符号和至少14个字符。强制用户每90天更新一次密码并进行设置,以便系统记住最近的24个密码。
这样的密码策略将阻止用户跨多个设备创建简单的密码,并防御大多数暴力攻击。
作为安全性最佳实践和保护的附加层,您还应该实现多因素身份验证。要求用户添加两个或更多证据以验证其身份。
使用云访问安全代理(CASB)
CASB的使用正迅速成为实现云安全最佳实践的中心工具。该软件位于您和您的云服务提供商之间,可以将您的安全控制扩展到云中。
CASB为您提供了一套完善的云安全工具集,以提供您的云生态系统的可见性,实施数据安全策略,实施威胁识别和保护以及维护合规性。
您可以在本指南的后面部分中详细了解CASB的工作方式,其中包括CASB排名前5位的提供商。
针对云客户的十大安全清单建议
迁移到云中并选择服务提供商时,您应考虑的最重要因素之一就是安全性。您将与所选的服务提供商共享和/或存储公司数据。
您需要确信自己的数据是安全的。从分担责任到提供商的安全标准是否达到极限,有无数的安全因素需要考虑。这可能是一个艰巨的过程,尤其是如果您不是安全专家。
安全永远不应被忽略!评估云服务提供商时,获取此十大安全方面的清单??
点击鸣叫
为了帮助我们评估云服务提供商时,编制了十大安全检查清单。
1.保护运输中的数据和静止数据
当迁移到云服务时,安全性的关键要素是保护您(最终用户)和提供商之间传输的数据。这对您和提供者都是双重责任。您需要网络保护来防止数据被拦截,并且需要加密来防止攻击者读取任何被拦截的数据。
寻找可以为您提供一套工具的服务提供商,以帮助您轻松地加密传输中和静止时的数据。这将确保对云服务提供商内部的任何内部数据传输,或云服务提供商与可能暴露API的其他服务之间的传输提供相同级别的保护。
2.资产保护
选择云服务提供商时,您需要了解存储,处理和管理数据的物理位置。在实施政府和行业法规(例如GDPR)之后,这一点尤其重要。
为了确保您的资产受到保护,好的提供商将在其数据中心内提供高级物理保护,以保护您的数据免遭未经授权的访问。他们还将确保在重新配置或处置任何资源之前先擦除您的数据资产,以防止其落入错误的人手。
3.可见性与控制
安全性的关键因素是查看和控制自己的数据的能力。优质的服务提供商将为您提供一种解决方案,无论您身在何处,都可以完全看到您的数据以及谁在访问数据。
您的提供商应提供活动监控,以便您发现整个生态系统中配置和安全性的变化。以及支持对新旧解决方案集成的合规性。
4.可信安全市场和合作伙伴网络
保护您的云部署将需要多个解决方案或合作伙伴。优秀的云服务提供商将使您轻松地通过市场查找并与不同的合作伙伴和解决方案建立联系。
寻找具有市场的提供商,该市场提供经过验证的安全合作伙伴具有可靠合作伙伴关系的精选网络。市场还应该提供安全性解决方案,这些解决方案提供一键式部署,并且可以在公共,私有或混合云部署中为保护数据提供补充。
5.安全的用户管理
优秀的云服务提供商将提供能够对用户进行安全管理的工具。这将有助于防止未经授权访问管理界面和过程,以确保应用程序,数据和资源不会受到损害。
云提供商还应提供功能来实施安全协议,以分隔用户并防止任何恶意(或受感染)用户影响另一个用户的服务和数据。
6.合规与安全集成
在考虑云服务提供商时,安全性和合规性是齐头并进的。它们应满足由第三方组织验证的全球合规性要求。您需要一个云服务提供商,该提供商遵循业界云安全最佳实践并理想地持有公认的认证。
云安全联盟的安全,信任和保证注册表(STAR)计划是一个很好的指标。此外,如果您在监管严格的行业中工作-可能适用HIPPA,PCI-DSS和GDPR-您还需要确定获得特定行业认证的提供商。
为确保合规性工作具有成本效益和效率,云服务提供商应为您提供将其安全控制继承到您自己的合规性和认证程序中的能力。
7.身份和认证
您的云提供商应确保对任何服务接口的访问仅限于授权和认证的人员。
在查看提供程序时,您需要一种提供身份和身份验证功能的服务,其中包括用户名和密码,两因素身份验证,TLS客户端证书以及与现有身份提供程序的身份联合。
您还希望能够限制对专用线路,企业或社区网络的访问。好的提供商只能通过安全通道(例如HTTPS)来提供身份验证,以避免被拦截。
确保避免使用身份验证做法较弱的服务。这将使您的系统遭受未经授权的访问,从而导致数据盗窃,服务更改或服务被拒绝。还要避免通过电子邮件,HTTP或电话进行身份验证。
这些漏洞极易受到社会工程和身份和身份验证凭据的拦截。
8.运营安全
选择云服务时,请寻找能够实现强大运营安全性以检测并防止攻击的提供商。这应该涵盖四个核心要素:
配置和变更管理
您希望提供程序在组成服务的资产(包括任何配置或依赖项)中提供透明性。他们应将可能影响安全性的任何服务更改通知您,以确保不会发生漏洞。
漏洞管理
您的提供商应具有漏洞管理流程,以检测和缓解对其服务的任何新威胁。您应随时了解这些威胁,严重性以及计划的缓解威胁时间表(包括解决方案)。
保护性监控
任何物有所值的提供商都将拥有高级监视工具,以识别服务的任何攻击,滥用或故障。他们将采取快速果断的措施来解决所有事件-使您随时了解结果。
在Kinsta,我们为WordPress托管解决方案提供最高的操作安全标准而感到自豪。 This includes implementing the latest security updates, continuous uptime monitoring, automatic backups, and active and passive measures to stop any attack in its tracks.
Bottom line: your site is monitored and secured 24/7.
Incident Management
Your ideal provider will have a pre-planned incident management process in place for common types of attacks. They will be ready to deploy this process in response to any attack.
There will be a clear contact route to you to report any incidents, with an acceptable timescale and format in place.
9. Personnel Security
You need a cloud service provider whose personnel you can trust, as they will have access to your systems and data. Your chosen cloud service provider will have a rigorous and transparent security screening process in place.
They should be able to verify their personnel’s identity, right to work, and check for any unspent criminal convictions. Ideally, you want them to conform to your countries locally established screening standard, such as BS 7858:2019 for the UK or completion of form I-9 in the US.
In addition to screening, you want a service provider who ensures their personnel understand their inherent security responsibilities and undergo regular training. They should also have a policy to minimize the number of people who have access to and can affect your services.
10. Secure Use of the Service
You can choose a cloud provider with cutting edge security and still experience a breach through poor use of the service. It’s important to understand where security responsibilities lie when using the service.
Your level of responsibility will be influenced by your cloud deployment model, how you use any services and the built-in features of any individual service.
For example, you have significant security responsibilities with IaaS. Deploying a compute instance, responsibility would fall to you to install a modern operating system, configure security, and ensure ongoing patches and maintenance. The same is true of any application you deploy on that instance.
So, make sure you understand the security requirements of your chosen service and any security configuration options available to you. Ensure you also educate your staff in secure use of your chosen services.
What is the Cloud Security Alliance?
When we look at the cloud computing industry, it’s a disparate market without a central governing body where businesses can go for guidance. This can be frustrating, especially when approaching challenges like cloud security.
Thankfully, in the place of governing bodies, there are a number of organizations that dedicate themselves to supporting the industry. The Cloud Security Alliance is one such organization.

Cloud Security Alliance Logo
The Cloud Security Alliance (CSA) is a non-profit organization dedicated to developing and raising awareness of best practices to maintain a secure cloud computing environment.
It is a membership organization offering the industry cloud-specific security guidance in the form of education, research, events, and products. This guidance is harnessed directly from the combined subject matter expertise of industry practitioners, associations, governments, and the CSA’s individual and corporate members.
To give you a better understanding of the Cloud Security Alliance, let’s take a closer look at how they support the industry.
Membership
The CSA is built on the foundation of its members. Joining the CSA as a member opens a range of different benefits depending on whether you’re an individual, enterprise, or solution provider.
Primarily these fall into similar categories including access to their expert network of other members, a seat on the International Standardization Council, discounts on training, and access to exclusive events and webinars
Assurance
The CSA has developed one of the most renowned cloud security certification programs: the Security, Trust & Assurance Registry (STAR).
STAR is a provider assurance program providing transparency through self-assessment, third-party auditing, and continuous monitoring against standards. The program comprises of three levels, demonstrating the holder adheres to best practices whilst validating the security of their cloud offerings.
教育
To support continual improvement of cloud security in the industry, the CSA offers a range of education services. You can pursue a range of cloud security certifications developed by the CSA, access their knowledge center, and take part in their regularly scheduled educational webinars and events.
研究
The CSA continues to support the industry developing and innovating cloud-security best practice through its ongoing research. This is driven by their working groups which now span 30 domains of cloud security.
Most recent and cutting edge include the emergence of working groups for DevSecOps, the Internet of Things, Artificial Intelligence, and Blockchain. The CSA continually publishes its research – free of charge – ensuring the industry can keep up-to-date and informed of the ever-changing nature of cloud security.
Community
The CSA also supports the industry by continuing to maintain and develop the cloud security community. They have created and maintain a wide range of communities which allow minds from across the cloud security industry to connect, share knowledge and innovate.
The CSA blog
These growing communities come in many forms. There CSA chapters you can join to connect with local professionals and CSA summits where the best minds share their expertise with the masses. There is even the CSA blog that hosts a community of followers wanting to keep pace with the CSAs practices.
What is Kaspersky Security Cloud?
When talking about cloud security, it’s easy to focus on enterprises and forget about the need for individual consumers.
If you’re accessing cloud services for your own personal use – photos, files, life admin – you need to think about the security of your data: Kaspersky Security Cloud, the new adaptive cloud-based security solution from Kaspersky.

Kaspersky Security Cloud
Combining the very best features and applications from Kaspersky Lab’s anti-virus software, it creates responsive protection for users’ devices against digital threats.
The platform was designed for individual users, not businesses.
Kaspersky Security Cloud protects your devices against malware and viruses, adding functionality to adapt how you use each device to provide maximum protection at all times. It offers features including antivirus, anti-ransomware, mobile security, password management, VPN, parental controls, and a range of privacy tools.
The platform is available on Windows, macOS, Android, and iOS. The Kaspersky Security Cloud Family plan offers protection for up to 20 devices.
Core Functionality in Kaspersky Security Cloud
To help you better understand the Kaspersky Security Cloud offering, we’ve taken a closer look at the core functionality within the platform which is split into four sections:
Scan
The critical functionality you want from any security solution, Kaspersky Security Cloud can scan your devices and remove any malware or viruses found. You can choose from a number of scanning options including individual files, quick scan, whole system, and scheduled.
Privacy
You can protect your privacy using built-in functionality to check your online accounts to ensure they are not compromised, block your webcam from being accessed, and block website traffic to prevent your browsing activities being monitored.
You can extend your privacy with additional downloads of Kaspersky Secure Connection and Kaspersky Password Manager. Secure Connection encrypts all data you send and receive while also hiding your location, while Password Manager stores and secures your passwords.
Home Network
Home Network gives you the visibility of all devices that are connected to your home network. Identifying those that are protected by Kaspersky Security Cloud. The functionality allows you to be notified when a new device connects and also block any unknown devices.
HD Health
Useful, yet simple, the HD Health functionality gives you a rating of you Hard Drives disk condition and disk temperature. Giving information on error rates, power cycles, power-on hours, total data read, and total data write.
Kaspersky Security Cloud is a great example of how the adoption of cloud services has created the need for new security solutions.
In the next section, we look at a similar example in the enterprise world with the arrival of Cloud Access Security Brokers.
What is a Cloud Access Security Broker (CASB)?
A Cloud Access Security Broker (CASB) is software that sits between you, the cloud service consumer, and your cloud service provider(s). A CASB extends your security controls from your on-premises infrastructure into the cloud. Helping to enforce security, compliance, and governance policies for your cloud applications. It typically sits on-premises or hosted in the cloud.
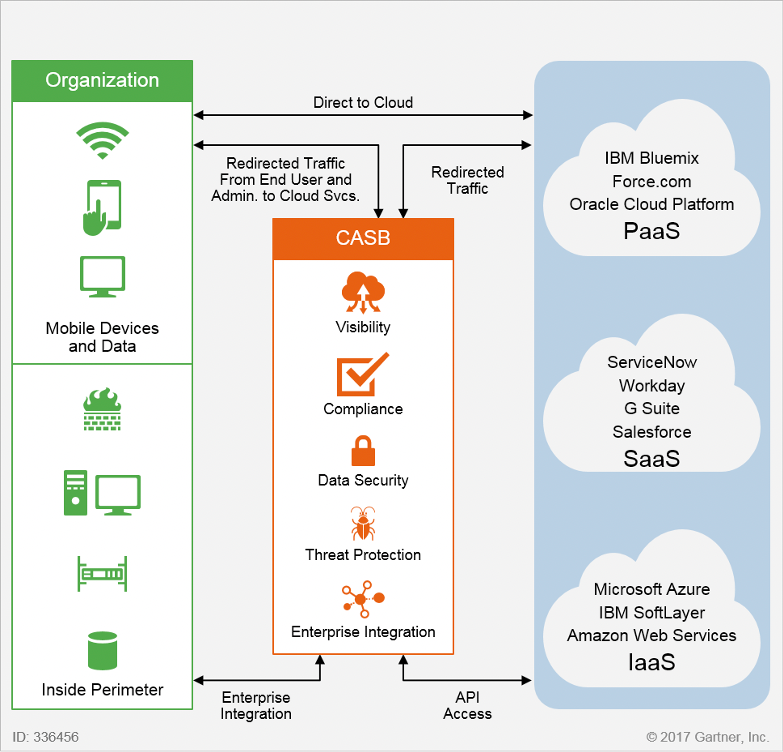
Cloud Access Security Broker Model (Image source: Gartner)
A CASB will help you defend against high-level cloud security risks and support ongoing monitoring and mitigation of high-risk events. It does this by securing the data moving between your on-premise and cloud environment using your organization’s security policies.
A CASB will protect you from cyberattacks with malware prevention and secure your data using end-to-end encryption preventing outside users from deciphering the content.
How does a CASB work?
A CASB can be deployed in three separate ways: as a reverse proxy, forward proxy, or in an ‘API mode’. Each has its own unique advantages and disadvantages, with many industry experts recommending a multimode deployment.
Let’s take a closer look at the different deployment modes of a CASB:
Reverse Proxy
A reverse proxy sits in front of the cloud service, providing inline security capabilities by sitting in the path of the network traffic. The connection of the reverse proxy broker runs from the internet to your application server, hiding information behind it that is coming from the original source.
Forward Proxy
A forward proxy sits in front of the user, with the CASB proxying traffic to multiple cloud platforms. The connection of the forward proxy runs from you, sat behind your firewall, to the internet. Like the reverse proxy, it also provides inline security capabilities.
API Mode
Unlike the proxy deployments, using the Application Program Interface (API) allows for direct integration of the CASB and a cloud service. This allows you to secure both managed and unmanaged traffic.
Depending on the cloud service providers’ API functionality, you can view activity, content, and take enforcement action.
The Pillars of Functionality in CASBs
A CASB delivers functionality which falls under four ‘pillars’, these include:
1. Visibility
When a cloud application sits outside the view of your IT department, you create information that is uncontrolled by your business’ governance, risk, and compliance processes.
A CASB gives you visibility of all cloud applications and their usage. Including vital information on who is using the platform, their department, location, and the devices used.
2. Data Security
Using a cloud platform creates an increased risk of inadvertently sharing data with the wrong people. If you’re using cloud storage, a typical data loss prevention (DLP) tool won’t be able to track or control who is accessing your data.
A CASB helps you to enforce data-centric security within a cloud platform combining encryption, tokenization, access control, and information rights management.
3. Threat Protection
One of the most difficult security threats to protect against is your own staff. Even former employees who’ve been disabled from your organization’s core systems may still be able to access cloud apps containing business-critical information.
CASBs allow you to detect and respond to malicious or negligent insider threats, privileged users, and compromised accounts within your cloud infrastructure.
4. Compliance
When your data moves to the cloud, you’ll need to ensure you maintain data security and privacy to comply with industry and governmental regulations. A CASB will do this for you, identifying and enforcing DLP policies on sensitive data in your cloud deployment. Helping you to maintain compliance with regulations including SOX and HIPAA.
A CASB will also help benchmark your cloud security configuration against core regulatory requirements like PCI DSS, NIST, CJIS, MAS and ISO 27001.
The Top 5 Cloud Access Security Brokers in 2020
The mass migration of services to the cloud paired with the need to implement cloud security due to the significant risks of data breach and loss has created an explosion in the CASB market.
As a next-generation technology, CASBs have become an essential element of cloud security strategy. With one in five large enterprises uses a CASB to secure or manage their cloud services, according to Gartner’s “Magic Quadrant for Cloud Access Brokers” report:
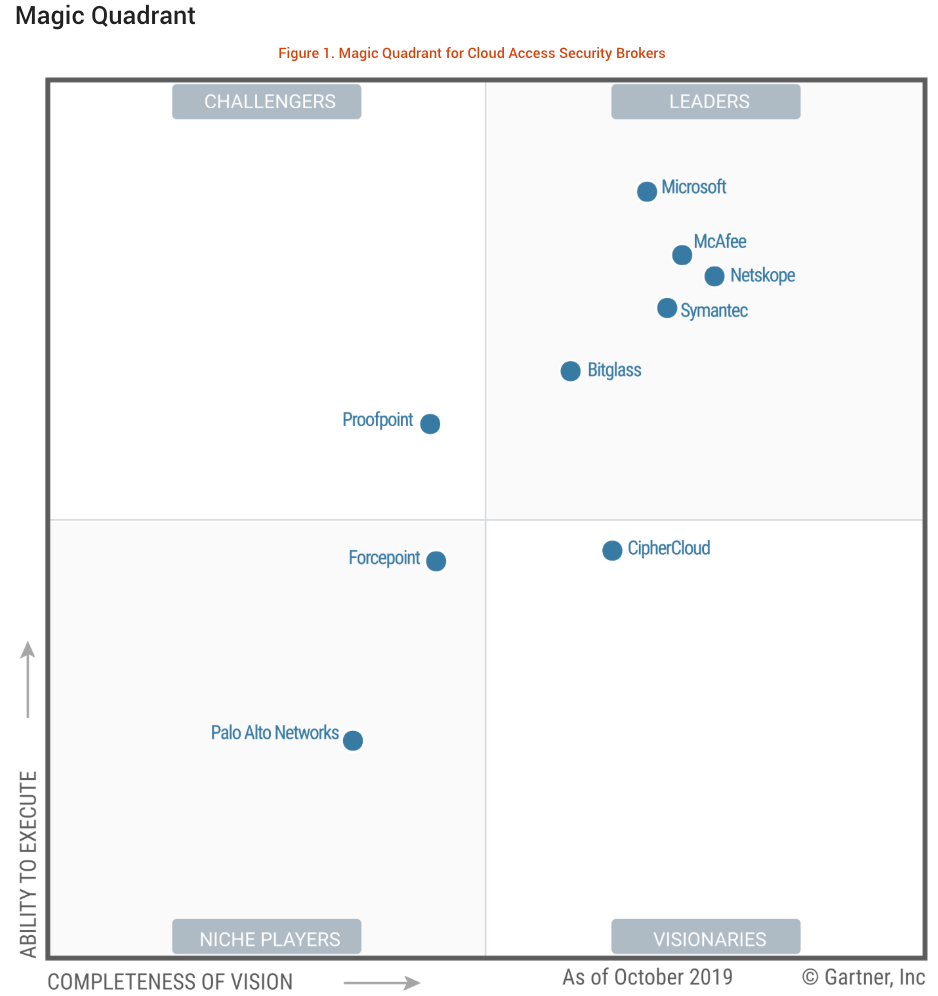
Gartner 2019 Cloud Access Security Broker (CASB) Magic Quadrant
Gartner has identified five the leaders in the CASB market using their ‘Magic Quadrant’, these include:
McAfee
McAfee entered the CASB market in January 2018, with its high profile its acquisition of Skyhigh Networks. Now known as MVISION Cloud, the platform provides coverage across all four CASB pillars for a broad range of cloud services.
The platform provides a comprehensive DLP engine and offers advanced controls including encryption, and tokenization of structured and unstructured data. The CASB can be deployed for API inspection with reverse-proxy-mode capabilities, and forward proxy.
McAfee has also made an on-premises virtual app available for those that require it.
Microsoft
Microsoft’s CASB offering is called Microsoft Cloud Application Security. The platform supports multiple deployment modes including reverse proxy and API connectors. Microsoft continues to develop the CASB solution with enhanced visibility, analytics, data control, and innovative automation functionality.
Microsoft Cloud Application Security also natively integrates with Microsoft’s growing portfolio of security and identity solutions including Azure Active Directory and Microsoft Defender Advanced Threat Protection.
This allows Microsoft to offer customers a fully integrated solution across their Microsoft platforms with single-click deployments.
Netskope
Unlike many players in the space who are simply acquiring CASB solution providers, Netskope remains an independent company. The provider is renowned for excellence in application discovery and SaaS security assessments.
Netskope supports thousands of cloud services through published APIs and inline decoding of unpublished APIs. The CASB offers DLP and identifies threats in real-time using combined threat intelligence, static and dynamic analysis and machine learning-based anomaly detection.
Symantec
Symantec’s CASB offering is called CloudSOC, enhanced in 2016 with the acquisition and integration of Blue Coat Systems’ Perspecsys and Elastica products.
CloudSOC offers DLP using automated data classification and multimode oversight using native cloud APIs, real-time traffic processing, and input from multiple data feeds. You can automatically identify and nullify threats from inside and outside your organization with advanced user behavior analytics (UBA).
Bitglass
Bitglass Cloud Security is referred to as a next-generation CASB, designed to integrate with any app, device, or network.
The platform runs natively from the cloud and is renowned as the only provider securing corporate data on mobile devices without using agents or profiles. Bitglass rose to prominence by introducing a zero-day approach focussed on trust ratings, trust levels and at rest encryption.
A Look at the Top 10 Cloud Security Certifications in 2020
To successfully protect your cloud platform, you’re going to need advanced cloud security skills and knowledge. You’ll also need to learn platform-specific skills so you can configure access, network security and ensure data protection all within your chosen cloud provider.
Thankfully, the cloud training and certification market continues to evolve and offer up a number of solutions. You can now choose from a wide range of platform-specific and vendor-neutral certifications to help you develop and prove the skills you need. Whether you’re looking to develop foundation knowledge or tailor your skillset to a specific job role, there is a certification for you.
To help in your search, we’ve compiled a list of the top 10 cloud security certifications to achieve in 2020.
Earning just one of these certifications will not only help you better secure your cloud deployment, but it’ll also make you more employable, and advance your salary.
(ISC)2 – Certified Cloud Security Professional (CCSP)
The CCSP is a globally recognized cloud security certification aimed at IT and Information Security leaders.
Earning the CCSP demonstrates you have the advanced technical skills and knowledge to design, manage and secure data, applications, and infrastructure in the cloud. You will do this using the best practices, procedures, and policies developed by cybersecurity experts at (ISC)2. The CCSP is ideal if you’re an Enterprise Architect, Systems Engineer, Security Administrator, Architect, Engineer, or Manager.
Before training and attempting the CCSP exam, you’ll need to meet some strict experience requirements. You’ll need five years full-time experience working in IT, including three years in cybersecurity and one year in one or more of the six domains of the CCSP CBK. You can substitute the experience requirements you hold the equally advanced (ISC)² CISSP credential – titled ‘The World’s Premier Cyber Security Certification.
Cloud Security Alliance – Certificate of Cloud Security Knowledge (CCSK)
The CCSK certificate is a widely-recognized entry-level certification in cloud security. It was developed by the Cloud Security Alliance, a member organization helping to ensure secure cloud computing environments by defining and raising awareness of industry best practice.
Earning the CCSK certification will prove you have the foundation skills and knowledge required to secure data in the cloud. You’ll learn how to build a baseline of security best practices mapped to a range of responsibilities from configuring technical security controls to cloud governance.
By becoming CCSK certified, you will also meet some prerequisite experience required if you intend to pursue the more advanced CCSP certification from (ISC)².
AWS Certified Security – Specialty
The AWS Certified Security – Speciality credential is ideal if looking to develop your career working with the AWS cloud platform.
By achieving the AWS Certified Security, you’ll validate your skills across data classifications, encryption methods, secure Internet protocols, and the AWS mechanisms required to implement them.
Working towards the certification, you can choose from a diverse learning pathway to shape your knowledge and skills across security fundamentals, architecting and security engineering on AWS. By the end of the pathway, you’ll have developed the control and confidence to securely run applications in the AWS Cloud.
To start working towards the credential, you should be in a security role and have at least two years of hands-on experience securing AWS workloads.
Microsoft Certified: Azure Security Engineer Associate
Recently, Microsoft transformed their certification pathways to be role-based. By earning one of their certifications, you are now proving you have the required skills and knowledge to perform a specific job role.
So, earning the Azure Security Engineer Associate certification shows you have the skills to be a Security Engineer on the Azure Cloud Platform. This includes the ability to protect data, applications, and networks in a cloud environment. Implementing security controls and threat protection as well as managing identity and access.
There are no prerequisite skills requirements before you attempt the AZ-500: Microsoft Azure Security Technologies exam.
Google Cloud – Professional Cloud Security Engineer
Earning Google’s Professional Cloud Security Engineer credential proves you can design, develop, implement, and manage secure infrastructure on the Google Cloud Platform. You’ll do this using Google security technologies aligned to security best practices and industry requirements.
By pursuing the Professional Cloud Security Engineer certification, you’ll need to learn how to configure access, network security and ensure data protection within the Google Cloud Platform. You’ll also need to develop knowledge to ensure compliance and managed operations.
Like the Azure and AWS certifications, this credential is ideal if you’re looking to develop cloud security skills specific to the Google Cloud Platform. Advancing your career with this leading cloud provider.
Alibaba ACA Cloud Security Certification
This ACA Cloud Security certification is the first in a certification pathway from Alibaba. Gaining this certification will prove you have the foundation knowledge to apply cloud security principles in an Alibaba cloud deployment.
You’ll develop fundamental skills with Linux and networking operations. While also learning about hosting, application, network and data security solutions all within the Alibaba Cloud Platform. You’ll cover several key security products from Alibaba including Server Guard, WAF, Anit-DDoS basic, and Pro.
After achieving the associate level certification, you can then pursue the Alibaba ACP Cloud Security certification.
Alibaba ACP Cloud Security Certification
The ACP Cloud Security certification is the second certification in the Alibaba cloud security pathway. It is a more advanced certification aimed at architects, developers and O&M professionals working with Alibaba Cloud security products.
Building on the foundation skills and knowledge achieved in the ACA Cloud Security certification, you’ll learn about Alibaba Cloud’s core products in security, monitoring, and management.
Once you have achieved the Professional level certification, you can then pursue the Alibaba ACE Cloud Security certification. Though the expert level certification is still in development and is expected to launch soon.
Cloud Credential Council – Professional Cloud Security Manager Certification (PCS)
The CCC Professional Cloud Security Manager credential is an advanced certification from the Cloud Credential Council. It’s ideally suited if you’re a governance and risk professional, auditor compliance specialist, or a cloud computing specialist.
Working towards the certification you will learn the skills and knowledge to apply best practices in a cloud environment for security and governance. Covering key topics like cloud service management, governance, and strategy. You’ll also learn how to design, deploy, and migrate a cloud service in a secure environment.
Due to the advanced nature of the certification, it is recommended you already hold the CCC Cloud Technology Associate and CCC Cloud Virtualization Essentials delivered by EXIN.
Oracle Cloud Platform Identity and Security Management 2019 Certified Associate
The title of Oracle’s cloud security certification is self-explanatory, you will learn about identity and security management on the Oracle Cloud Platform. Ideal if you’re a security professional looking to demonstrate their expertise in implementing cloud solutions.
Preparing for the certification, you’ll cover core security functionality in the Oracle cloud platform. Building knowledge and skills to implement Oracle Identity Cloud Service, Oracle CASB Cloud Service, services Architecture and Deployment, and Identity Security Operations Center Framework
Passing the 1Z0-1070 exam will certify you as an Oracle Certified Associate (OCA), a globally recognized credential. You will validate your capabilities with the Oracle Cloud Security portfolio, including configuration of the services. Before getting started, you’ll need up-to-date and hands-on experience with Cloud Security implementations in an administrator role.
SANS SEC524: Cloud Security and Risk Fundamentals
The SEC524: Cloud Security and Risk Fundamentals is a course, not a certification. I’ve included it regardless as it teaches vital skills and knowledge not covered by the other certifications listed.
Most importantly, you’ll learn how to evaluate the security of different cloud providers. Covering the cloud computing delivery models – SaaS, PaaS, and IaaS – and their unique security requirements. As well as additional security considerations when operating in a public, private, or hybrid cloud scenario.
Finishing the course you’ll come away with a range of key abilities. How to assess cloud contracts, adapt security architecture, tools, and processes for use in cloud environments and perform vulnerability assessments of your cloud setup.
Cloud security is a complex interaction of technologies, processes, and policies. Get to know the top 10 security recommendations for cloud customers (and best practices) ☁️?
Click to Tweet
Summary
Moving to the cloud, you need to be ready to implement a comprehensive cloud security strategy from day one. This starts with identifying the right cloud service provider(s) and then implementing a strategy combining the right tools, processes, policies and best practices.
It is fundamental you understand your shared responsibility and focus on compliance.
In cloud security, your staff — or your cloud provider’s — are among the most critical and often overlooked aspects of defense against cybercriminals.
It’s important to remember that cloud computing is no less secure than deploying your services on-premises. In fact, many cloud providers offer advanced security hardware and software you would otherwise not have access to.
Choosing the right provider will improve your security stance and reduce your risks, regardless of those introduced by cloud computing.
If you enjoyed this article, then you’ll love Kinsta’s WordPress hosting platform. Turbocharge your website and get 24/7 support from our veteran WordPress team. Our Google Cloud powered infrastructure focuses on auto-scaling, performance, and security. Let us show you the Kinsta difference! Check out our plans
